One thing is sure, we're not kidding with the security vulnerabilities, and our goal is to be completely transparent with the users about the issues as soon as they are public (ie with a new version, a fix/patch or at least a workaround available).
In this context, the security page has been redesigned from scratch, it is more user-friendly and a lot of new information has been added about each vulnerability.
The URL is unchanged: https://weechat.org/doc/security/.
Among the new information:
- A "WSA" identifier (WeeChat Security Advisory), which is unique by vulnerability, and built like this:
WSA-YEAR-ID (YEAR on 4 digits, and the ID starts to 1 for the first vulnerability of this year, 2 for the second, etc.).
- The CVSS vector, score and severity, for more information:
- The vulnerability type, also known as CWE (Common Weakness Enumeration), for more information: https://cwe.mitre.org/
- The short description of the issue.
- The scope: which part of WeeChat is affected: it can be one or multiple plugins or features.
- More detailed information about the mitigation for the issue.
- The credit: who found the issue and reported it to WeeChat security team (displayed only with the agreement of the reporter).
Important: due to the way the CVSS vector, score and severity are computed, the severity level previously displayed has changed for some vulnerabilities and is now higher:
- WSA-2021-1 (Crash on malformed websocket frame in relay plugin): medium -> high (score: 7.5)
- WSA-2020-3 (Buffer overflow on new IRC message 005 with nick prefixes): low -> high (score: 7.5)
- WSA-2020-2 (Crash on malformed IRC message 352 (WHO)): low -> high (score: 7.5)
- WSA-2020-1 (Buffer overflow on malformed IRC message 324 (channel mode)): low -> high (score: 7.5)
- WSA-2013-3 (Crash on IRC commands sent via Relay): medium -> high (score: 7.5)
- WSA-2013-2 (Crash on send of unknown commands to IRC server): low -> medium (score: 5.5)
- WSA-2013-1 (Crash on nicks monitored with /notify): low -> medium (score: 5.5)
- WSA-2006-1 (Crash in API function infobar_printf): low -> medium (score: 6.2)
- WSA-2004-1 (Buffer overflows in build of strings): low -> medium (score: 6.2)
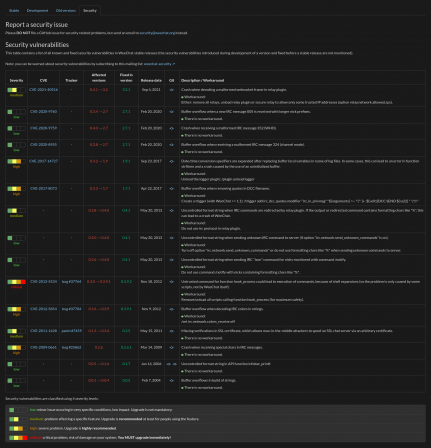
The page is now separated into two parts: the overview with only part of the info, and detail of each vulnerability below.
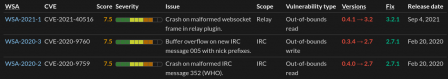
The overview shows synthesized data (click for full size):
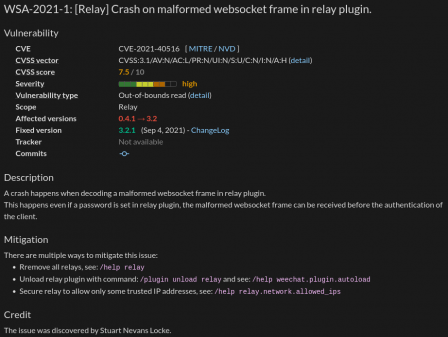
Below this, the detail of each vulnerability is displayed, for example this detail about the latest security vulnerability, fixed in version 3.2.1 (September 2021):
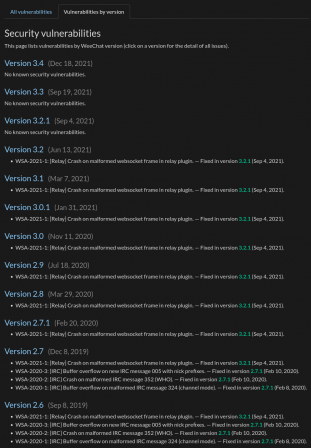
For convenience, a list of vulnerabilities by WeeChat version is also available:
For the record and reference (especially old severities), the previous security page was: